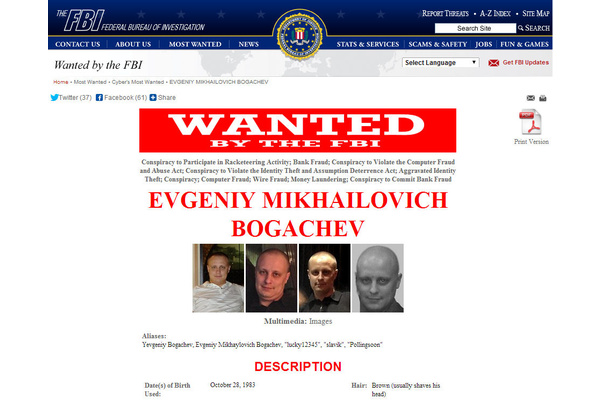
As we reported yesterday, a U.S./FBI-led international effort significantly disrupted the operation of the Gameover ZeuS botnet, which uses peer-to-peer communications and encryption to send commands from administrators around the network, and to send sensitive financial information from victims browsing activity back to the bot herders.
This malicious network may have already cost consumers and businesses over $100 million, and for those victims that have not used financial services while infected, the Crptolocker ransomware may have been installed in order to extort money by encrypting personal files until a fee is paid.
You can read about how the Feds and their international equivalents worked with private companies to disrupt the botnet here.
How to avoid infection & remove GOZeuS
Trojan.Zbot spread primarily through rogue e-mail attachments that when opened, download the malicious software and infect the computer, making it part of a wider botnet that is up to 1 million PCs strong. Avoiding infection simply requires vigilance when going through e-mail.
For those already infected, some regular anti-virus may not help you as more recent variations of it use a low-level driver component that can make detection difficult. Therefore, it is necessary to use more targeted removal tools along with regular A/V tools to clean up this mess.
We recommend using the Trojan.Zbot Removal Tool from Symantec (a.k.a Necrus Driver Removal Tool), which can remove the Necurs rootkit that Gameover ZueS uses to protect itself. The fix tool is available for both 32-bit and 64-bit Windows PCs. (Here's how to tell if your Windows is 32-bit or 64-bit)
Symantec Trojan.Zbot Removal Tool (32-bit): https://www.afterdawn.com/software/security/misc_security_tools/trojan_zbot_removal_tool.cfm
Symantec Trojan.Zbot Removal Tool (64-bit): https://www.afterdawn.com/software/security/misc_security_tools/trojan_zbot_removal_tool_64-bit.cfm
NOTE: This tool does not bring back files encrypted by Cryptolocker.
Download the tool for the appropriate operating system type, then remember that you must run it with Administrator privileges (right click - Run as Administrator). Close everything else you are using. You should also disable System Restore temporarily if running Windows XP (Control Panel -> System -> System Restore Tab). The first thing you need to do is accept the license agreement, and then you'll get to the main UI of the removal tool.
Eventually the tool will prompt you to restart your computer, and it may do this multiple times depending on your circumstances. After a reboot, run the tool again to clean threat artifacts. When the tool is done, it will prompt you to check a logfile that it created and ask you if you wish to run Norton Power Eraser for additional clean-up.
Both are optional to you at this point, but you should definitely run some kind of anti-virus tool after this process for additional cleanup. The logfile created by the tool is titled "Fixtool.log", and it will look something like this.
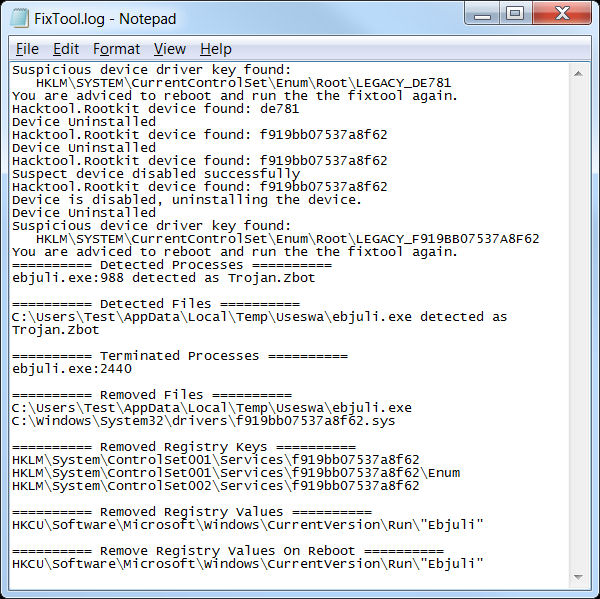
NOTE: For those who would prefer to run from command-line, check this article at symantec.com.
Plenty of options for anti-virus tools to install and run after this process is complete are available from www.afterdawn.com/software/security/antivirus/, including plenty of free options.
There are also plenty of other removal tools that target this specific rootkit & malware if you don't think this worked out.
Sources and Recommended Reading:
Two-week opportunity for UK to reduce threat from powerful computer attack: www.nationalcrimeagency.gov.uk
Log picture & software source: www.symantec.com
Written by: James Delahunty @ 3 Jun 2014 8:23
