How to remove a Bootkit?
 This guide shows how to quickly check for, and remove a Bootkit infection from your computer. It uses freely available software and should be easy enough for even novice users to understand. A Bootkit infects the Master Boot Record (MBR) on a HDD, and therefore is usually completely undetected by most anti-virus packages.
This guide shows how to quickly check for, and remove a Bootkit infection from your computer. It uses freely available software and should be easy enough for even novice users to understand. A Bootkit infects the Master Boot Record (MBR) on a HDD, and therefore is usually completely undetected by most anti-virus packages.What do I need?
You need to download a program called TDSSKiller from AfterDawn. TDSSKiller is developed by Kaspersky and distributed for free. It specializes in the removal of TDSS rootkit infections, though it can remove many other rootkits that use particular means to hide themselves within a Windows operating system. It can also remove bootkits which use the boot sector.
Download: TDSSKiller
What is a Bootkit?
A Bootkit is malicious code that is injected into the Master Boot Record (MBR) of a hard disk drive. This allows the malware to run before the operating system is even loaded, as soon as the BIOS initiates it.
Once a bootkit has decrypted its own files in its own file system in unallocated disk space, it hands off control to the legitimate boot loader and the boot of the operating system commences.
A Bootkit is designed to hide from typical anti-virus and other security software suites. Some bootkits can even protect themselves by returning false information when an attempt is made to read the Master Boot Record.
Generally bootkits are used as part of a wider malware infection as one way to keep the system compromised.
TDSSKiller
TDSSKiller from Kaspersky is not just a great utility for removing rootkits from the Alureon family (as well as others), it can also check the Master Boot Record (MBR) and has the ability to restore it to a legitimate and safe Master Boot Record (MBR) right from a friendly Graphical User Interface.
The software is primarily designed to aid in the discovery and handling of rootkit files which include hidden system drivers and services, infected system files, hidden files on disk and more. It is a light-weight utility that packs a heavy punch and is available for free thanks to the work of Kaspersky.
TDSSKiller should be run as an Administrator on Windows Vista or 7.
TDSSKiller Scan
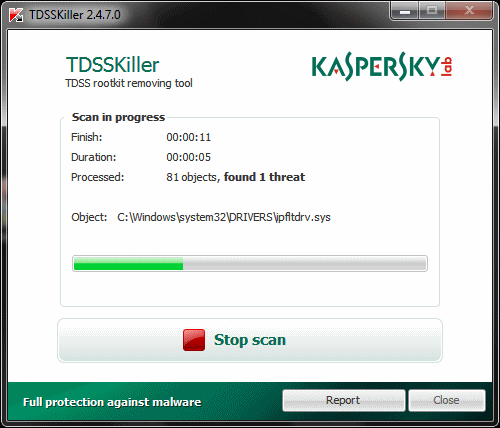
Clicking Start Scan will get the process going. The software will check through driver files for evidence of infection, or drivers / services that are suspiciously hidden. It will also check the Master Boot Record (MBR) of the hard drives connected to your system.
Depending on how badly infected a system is with malware, the scan may take some time to complete, but on most systems it really should only take a few seconds.
TDSSKiller Results
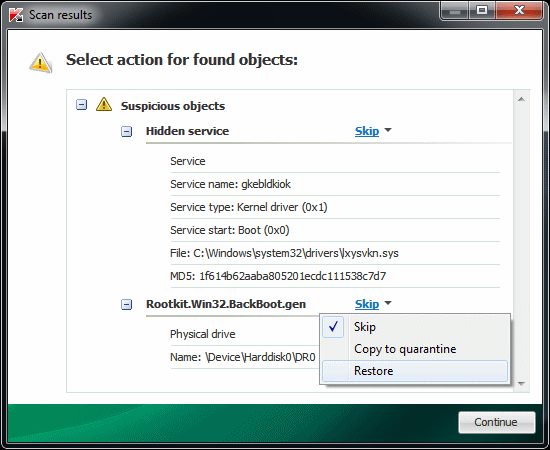
TDSSKiller offers two different types of results; Malicious and Suspicious.
A Bootkit will almost always be listed as a suspicious result, usually identified as Rootkit.Win32.BackBoot.gen. This is a suspected MBR infection.
For other types of results, Malicious Results are confirmed malware infections. These are very serious results. Suspicious Results will often include files that are hidden from the operating system, or hidden device drivers and/or system services that have not been detected as any particular type of malware.
What action to take?

In the example picture above, one of the results is identified as Rootkit.Win32.BackBoot.gen. This is a suspected Master Boot Record (MBR) bootkit infection. Once you get this result, choosing an Action of Restore (instead of the default Skip) is the recommended course of action. This will, as the name suggests, restore a legitimate Master Boot Record (MBR) and will stop the malware from executing before the operating system even starts loading.
For all other results from TDSSKiller.
For Malicious Objects, TDSSKiller will automatically select either Cure or Delete. In the case of an infected (yet vital) system file, TDSSKiller may choose to Cure the object, whereas a hidden driver or service that is entirely malware may be selected automatically as Delete.
For Suspicious Objects, the default action to be safe is "Skip". One thing you can do here is Quarantine an object so it is not deleted. It will be saved to the C:\TDSSKiller_Quarantine\ directory. You could now scan this directory with an anti-malware product to see what result you get, or even better, upload the suspicious file to VirusTotal to see results from a wide variety of A/V engines. You can also decide to delete an object if you wish.
To change the Action, simply click the blue action test shown beside the result (in the example picture it was Delete and Cure.
Reboot
Upon the removal of a bootkit (restoration of a legitimate Master Boot Record) you may be promted to reboot your computer with TDSSKiller.
